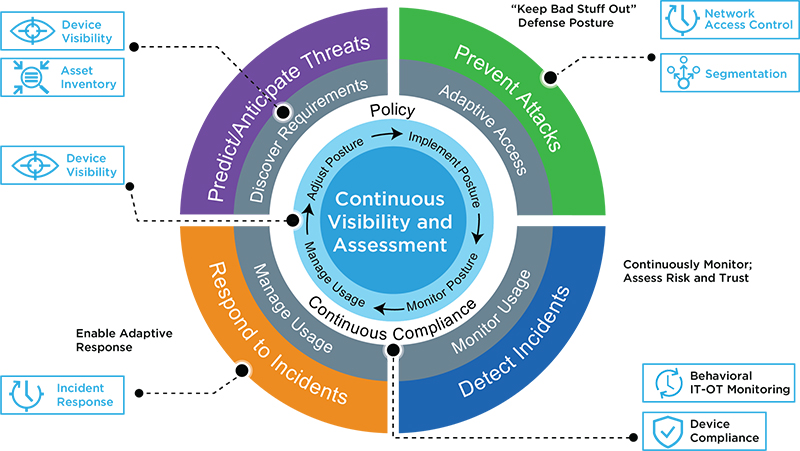
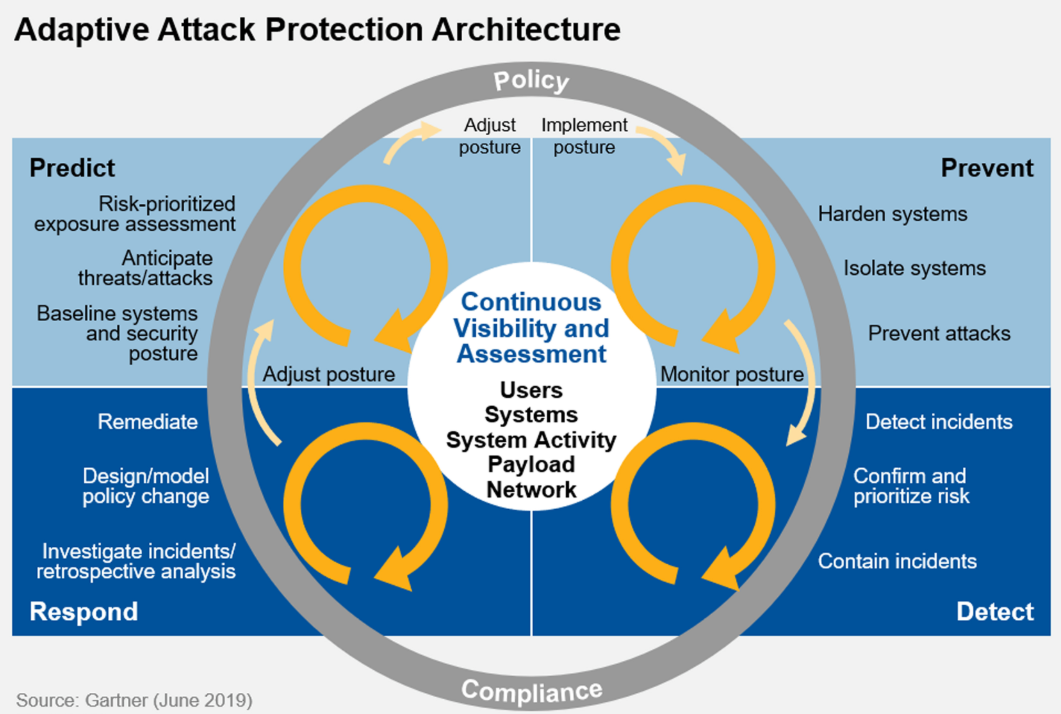
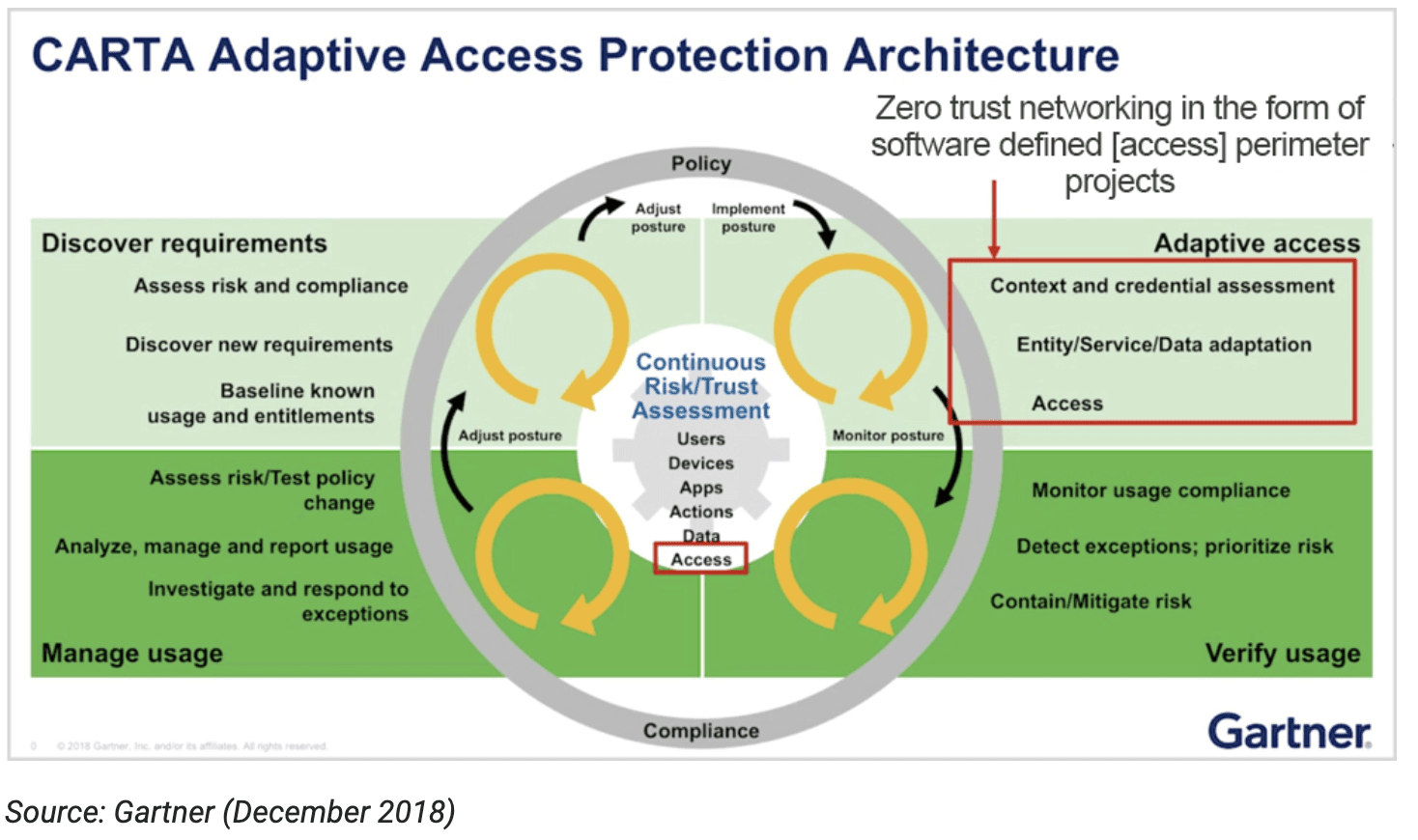
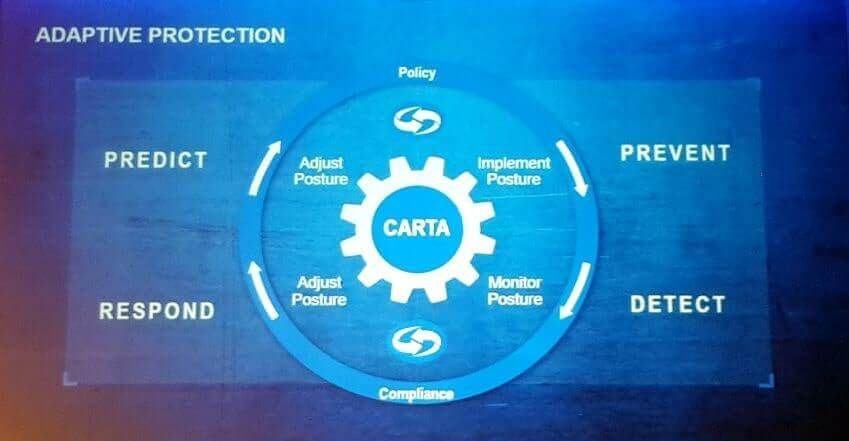
inWebo on Twitter: ". @Gartner_IT sees #CARTA as a way for organizations to manage risks arising from the digital world by deploying an agile security posture. Why inWebo #MFA is aligned with

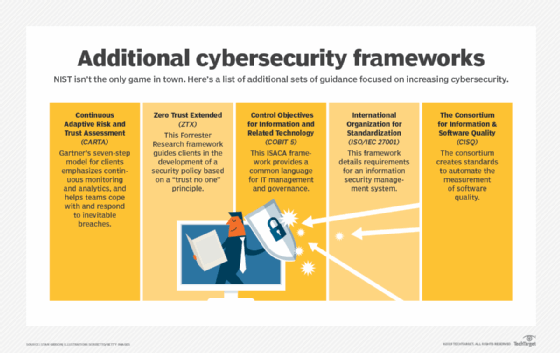
The three main ingredients for the successful implementation of zero trust in the time of COVID-19: Machine learning, carta and software defined perimeter | 2020-09-15 | Security Magazine